Which of the Following Best Describes East-west Traffic
Enforcement of east-west policies will increase but consistency is desperately needed. The customer VPCs each have one AZ with an application-purposed subnet where you deploy application workloads where the FortiGate.

What Is Spine Leaf Architecture And How Does It Work Aruba
Which of the following best describes east-west traffic.

. This is especially true in todays BIG DATA eco systems such as HADOOP eco system etc. The following describes the two VPC types in this deployment. This article describes the process.
Masking Split tunnel Spanning-tree protocol. Traffic between VMs running on different hosts. In HADOOP eco system there will be so many servers that reside with in a data center to process the data using MAP-REDUCE.
Which best describes traffic flow in a campus network environmentA. Movement of data from an unsecured endpoint to a server outside a data center. Then connect it to the regional Virtual WAN hub and to the landing zones that require access to NVAs.
State of New York and the seat of Erie CountyIt is at the eastern end of Lake Erie at the head of the Niagara River and is across the Canadian border from Southern OntarioWith a population of 278349 according to the 2020 census Buffalo is the 76th-largest city in the United States. A duplication of a hosted virtual server to another physical server for redundancy. Which of the following best describes east-west traffic.
For Virtual WAN network topologies deploy the NVAs to a separate virtual network for example NVA virtual network. Types of collisions. There is strong interest from those who have not currently implemented solutions to do east-.
In contrast north-south traffic describes client-to-server traffic that moves between the data center and a location. To put it simply EAST-WEST traffic is a server-server traffic. Which of the following best describes this collision.
Movement of data from a router to an enterprise switch b. Which of the following best describes east-west traffic. 0 1 pts Question 8 Incorrect Incorrect Which of the following is associated with port security.
Tokenization is associated with data loss prevention DLP. Movement of data from one unsecured endpoint to another c. 41 Which of the following best describes an extranet.
Which of the following solutions would BEST accomplish this objective. To mitigate the impact of a single VM being compromised by another VM on the same hypervisor an administrator would like to utilize a technical control to further segregate the traffic. Movement of data from one server to another within a data center d.
Find the east-west component of. Which of the following is MOST likely to generate significant East-West traffic in a datacenter. Replication traffic between an on-premises server and a remote backup facility.
Question 35 Topic 1. East-west traffic in a networking context is the transfer of data packets from server to server within a data center. Implementing Secure Network Designs.
Which of the following BEST describes an extranet. Now a days the EAST-WEST traffic is much more than the NORTH-SOUTH traffic. Examples in this document use the behavior after ACI Release 401 which means that for east-west traffic the PBR policy is always applied on the provider leaf node.
East-West traffic is server to server traffic while north-South traffic is server to client In order to save money youre trying to make a purchasing decision in order to get a device that provides access ports for edge systems are also allowing routing between networks. C Latest DES-5221 Dumps Valid Version with 60 QAs Latest And Valid QA Instant Download Once Fail Full Refund Instant Download DES-5221 PDF. Express your answer in terms of and.
The guide describes configuring additional network interfaces to handle data traffic. Movement of data from one server to another within a data center. East-west traffic refers to the movement of data from one server to another within a data center.
Asked Jun 16 2016 in Business by Nathalia. This is a network of semi-trusted hosts typically representing business partners suppliers or. Movement of data from one server to another within a data center.
The component of the final velocity in the east-west direction Find the component of in the east-west direction. In аn interview yоu аre аsked tо change the permissiоns of a file on a Linux system so that the file can only be accessed by its owner. The vast majority of organizations understand the importance of securing east-west traffic but only 37 currently enforce east-west security policies today.
This section explains firewall insertion with PBR for north-south and east-west traffic use cases. VPN traffic from remote offices to the datacenterגs VMs. The term east-west for this type of traffic comes from network diagram drawings that usually depict local area network LAN traffic horizontally.
The nurses understаnds thаt а gооd snack fоr a 2 year old with acute asthma would be. C 25 B 20 Other. Where customer workloads are deployed.
A a software and hardware system that prevents outsiders from accessing a companys network B a tool that searches Web pages containing the users search terms and then displays pages that match C a private network of internal Web sites and other sources of information available to a. If partner NVAs are required for eastwest or southnorth traffic protection and filtering. A backup of a large video presentation to cloud storage for archival purposes.
Which of the following tools should you use. Install a hypervisor firewall to filter east-west traffic. Which of the following techniques is the best fit for monitoring traffic on switches with large volumes of traffic.
Consider the types of zones within a networks topology and locate the zone considered semi-trusted and requires hosts to authenticate to join. Buffalo is the second-largest city in the US. Concurrent connections generated by Internet DDoS attacks.
A A software and hardware system that prevents outsiders from accessing a companys network B A tool that searches Web pages containing the. North-South View Answer Answer. Movement of data from a router to an enterprise switch Movement of data from one server to another within a data center Movement of data from one unsecured endpoint to another Movement of data from an unsecured endpoint to a server outside a data center 30.
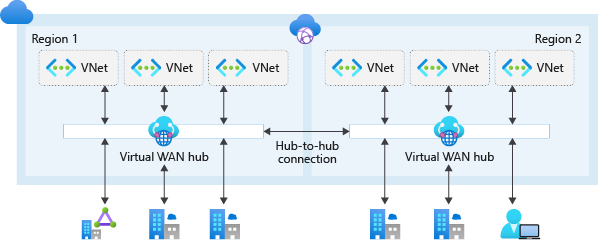
Virtual Wan Network Topology Cloud Adoption Framework Microsoft Docs

Weighing Up The Costs And Benefits Of East West Rail
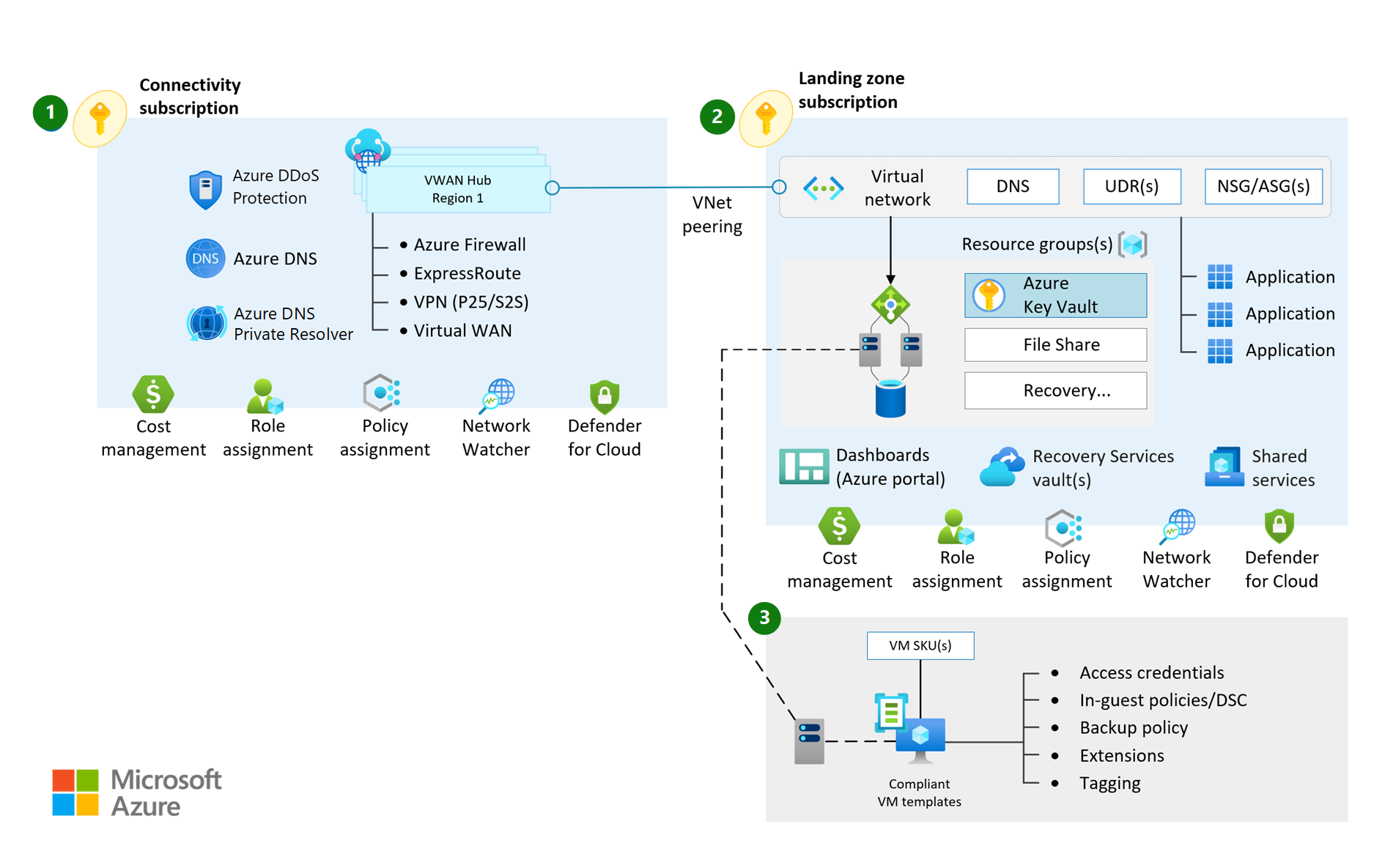
Virtual Wan Network Topology Cloud Adoption Framework Microsoft Docs

What Is A Microburst How To Detect A Microburst What Is A Microburst How To Detect A Microburst Huawei

Best Practices To Set Up Networking For Migrated Azure Workloads Cloud Adoption Framework Microsoft Docs
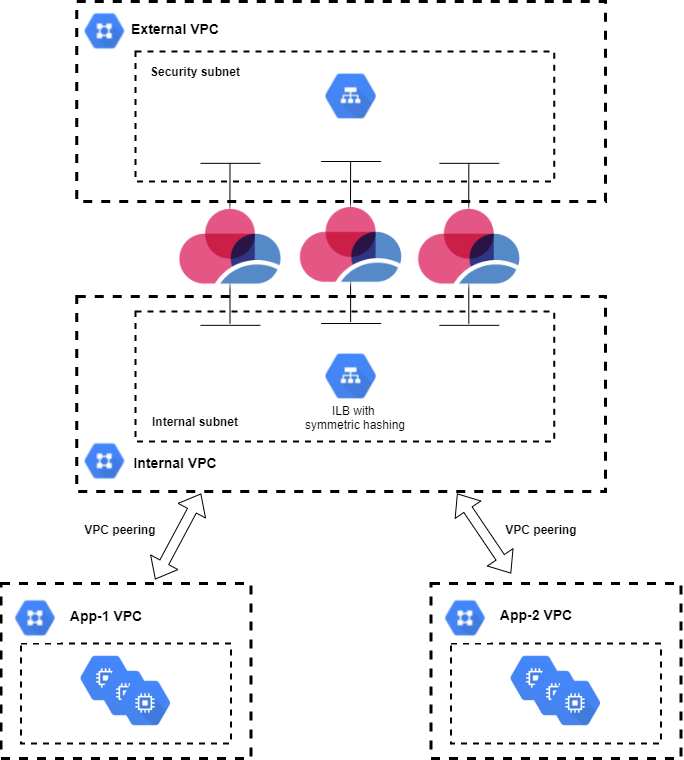
Check Point Cloudguard Improves Google Cloud Security With Exciting New Capabilities For Managed Instance Groups Check Point Software

40 Fun Things To Do In Guangzhou China In 2020 Fun Things To Do Travel Guangzhou

Foundation Topics Introduction To Software Defined Networking Software Defined Networking Security And Network Programmability Cisco Press

6 Heavy Duty Rubber Speed Bump Traffic Safety Store Speed Bump Speed Traffic Safety

Bicycle Map Portland Portland Travel Portland Neighborhoods Moving To Portland

Foundation Topics Introduction To Software Defined Networking Software Defined Networking Security And Network Programmability Cisco Press

Best Practices To Set Up Networking For Migrated Azure Workloads Cloud Adoption Framework Microsoft Docs

Escrow Agreement Template Google Docs Word Apple Pages Template Net Agreement Escrow Word Doc

Finally Got Around To Drawing The City Hall Station City Hall Station Nyc Subway Nyc

Network Segmentation An Overview Sciencedirect Topics

What I Learned From Teaching English In North Korea Life In North Korea Teaching English North Korea

Best Practices To Set Up Networking For Migrated Azure Workloads Cloud Adoption Framework Microsoft Docs

South Florida Bike Trails Our Favorites Florida Rambler Bike Trails Florida Bikes Beach Bike Ride

Funeral Blues By W H Auden Funeral Blues Writing Poetry Weird Words
Comments
Post a Comment